In this guide, we will show you how to install and bind a free TLS/SSL Let’s Encrypt certificate for a site on the IIS web server running on Windows Server 2019/2016/2012 R2.
Let’s Encrypt and ACME Clients for Windows
An TLS/SSL certificate of a website allows to protect user data transferred over the public network against man-in-the-middle (MITM) attacks and provides data integrity. Nonprofit certification center Let’s Encrypt allows you to automatically issue free X.509 encryption TLS certificates for HTTPS encryption using the API. Only certificates for domain validation that expire in 90 days are issued (there is a limit of 50 certificates for one domain per week). But you can automatically renew the SSL certificate for your website using simple scheduling.
The Let’s Encrypt API interface to automatically issue the certificates is called Automated Certificate Management Environment (ACME) API. There are 3 most popular ACME API client implementations for Windows systems:
- Windows ACME Simple (WACS) is the command prompt tool for the interactive issue an SSL certificate and bind it to a specific site on your IIS web server;
- Powershell ACMESharp module – is the PowerShell library with a number of cmdlets to interact with Let’s Encrypt servers over ACME API;
- Certify is a Windows graphics tool to manage SSL certificates interactively using ACME API.
WACS Clint to Install Let’s Encrypt TLS Certificate in IIS on Windows Server
The easiest way to get an SSL certificate from Let’s Encrypt is to use the console tool Windows ACME Simple (WACS) (previously this project called LetsEncrypt-Win-Simple). It is a simple wizard that allows you to select one of the websites running on the IIS, and automatically issue and bind an SSL certificate to it.
Suppose, you have an IIS website running on Windows Server 2016. Your task is to switch the website to an HTTPS mode by installing a free SSL certificate from Let’s Encrypt.
Download the latest release of the WACS client from GitHub https://github.com/PKISharp/win-acme/releases (in my case, this is version v2.0.10 – the file name is win-acme.v2.0.10.444.zip).
Extract the zip archive to the following directory on the server where IIS is installed: c:\inetpub\letsencrypt
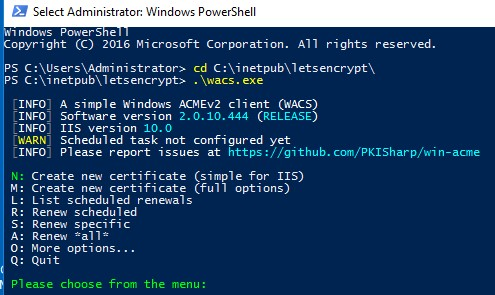
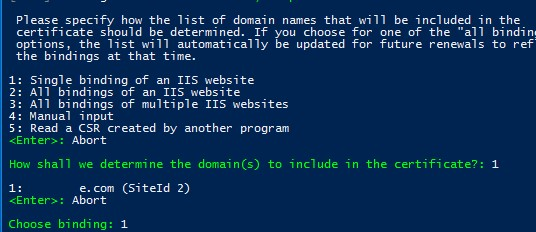
Open the elevated command prompt, go to c:\inetpub\letsencrypt directory, and run wacs.exe. This will launch an interactive Let’s Encrypt certificate generation and binding to the IIS site wizard. To quickly create a new certificate, select N: – Create new certificates (simple for IIS).
Next, you need to select the certificate type. In our example, there is no need to use a certificate with aliases (multiple SAN – Subject Alternative Name), so just select item 1. Single binding of an IIS site. If you need a Wildcard certificate, select the option 3.
Then the utility displays the list of websites running on IIS and prompts you to select a site to issue the certificate for.
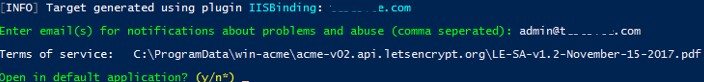
Specify the email address to which notifications about certificate renewing problems and other critical messages and abuses will be sent (you can specify multiple email addresses separated by commas). It remains to agree to the terms of use and Windows ACME Simple will connect to Let’s Encrypt servers and try to automatically generate a new SSL certificate for your website.
The process of generating and installing SSL Let’s Encrypt certificate for IIS is fully automated.
By default, domain validation is performed in the http-01 validation (SelfHosting) mode. To do this, you must have a domain DNS record pointing to your web server. When running WACS in manual mode (full options), you can select the validation type – 4 [http-01] Create temporary application in IIS (recommended). In this case, a small application will be created on the IIS web server through which Let’s Encrypt servers will be able to perform domain validation.
The WACS tool saves the private key of the certificate (*.pem), the certificate itself, and several other files in the C:\Users\%username%\AppData\Roaming\letsencrypt-win-simple. Then it will install the Let’s Encrypt SSL certificate generated in the background and bind it to your IIS site. If there is an SSL certificate installed on the site (for example, a self-signed cert), it will be replaced with a new one.
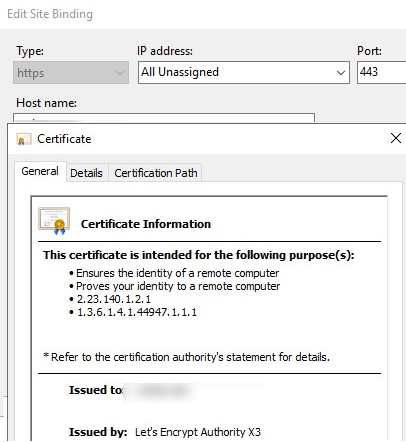
In IIS Manager, open the Site Binding settings for your website and verify that it uses the certificate issued by Let’s Encrypt Authority X3.
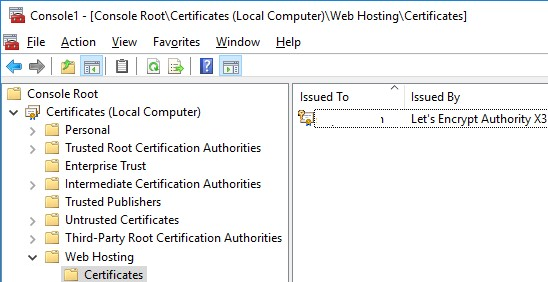
You can find the Let’s Encrypt IIS certificate in the computer certificate store under Web Hosting -> Certificates.
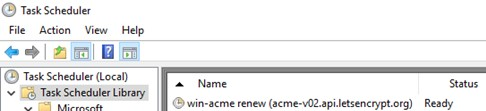
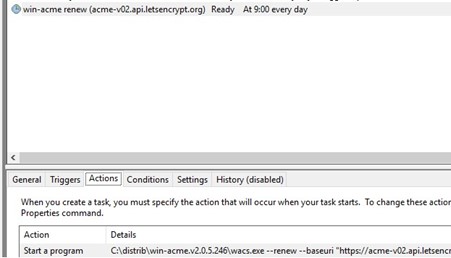
Windows ACME Simple creates a new job in the Windows Task Scheduler (win-acme-renew (acme-v02.api.letsencrypt.org)) to automatically renew the certificate. The task starts every day, and the renewal of the certificate is performed after 60 days. This task runs the command:
C:\inetpub\letsencrypt\wacs.exe --renew --baseuri "https://acme-v02.api.letsencrypt.org"
You can use the same command to manually update the Let’s Encrypt certificate.
Redirect from HTTP to HTTPS Using the IIS URL Rewrite
To redirect all incoming HTTP traffic to the HTTPS website URL, install the Microsoft URL Rewrite Module (https://www.iis.net/downloads/microsoft/url-rewrite), and make sure that the option Require SSL is disabled in the site settings. Now configure the redirect in web.config with rewrite rules:
<system.webServer>
<rewrite>
<rules>
<rule name=”HTTP to HTTPS Redirect” enabled=”true” stopProcessing=”true”>
<match url=”(.*)” />
<conditions>
<add input=”{HTTPS}” pattern=”off” ignoreCase=”true” />
</conditions>
<action type=”Redirect” url=”https://{HTTP_HOST}/{R:1}” appendQueryString=”true” redirectType=”Permanent” />
</rule>
</rules>
</rewrite>
</system.webServer>
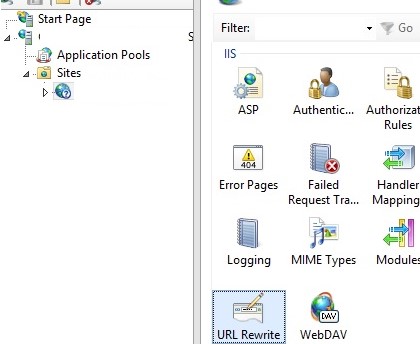
You can also configure traffic redirect using the URL Rewrite extension through the IIS Manager GUI. Select Sites -> yoursitename -> URL Rewrite.
Create a new rule Add Rule -> Blank rule.
Specify a rule name and change the following parameter values:
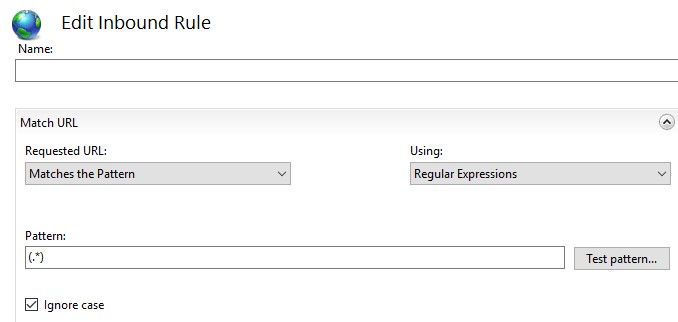
- Requested URL: Matches the Pattern
- Using: Regular Expressions
- Pattern: (.*)
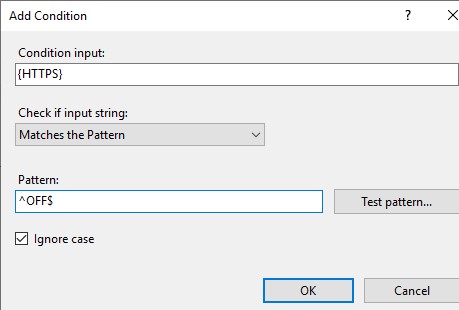
In the Conditions section, change the Logical Grouping: Match All and click Add. Specify the following settings:
- Condition input: {HTTPS}
- Check if input string: Matches the Pattern
- Pattern: ^OFF$
Now in the Action block select:
- Action Type: Redirect
- Redirect URL: https://{HTTP_HOST}/{R:1}
- Redirect type: Permanent (301)
Open a browser and try to open your site with an HTTP address; you should be automatically redirected to the HTTPS URL.
Using Let’s Encrypt Certificates with RDS Gateway & Web Access
If you use RDS Gateway or RDS Web Access to connect external users to the corporate network, you can use the trusted SSL certificate from Let’s Encrypt instead of the self-signed certificate. Consider how to correctly install the Let’s Encrypt certificate to secure Remote Desktop Services on Windows Server.
Then, run wacs.exe on the RD Gateway server, as described above. Select the desired IIS site (usually it is the Default Web Site. Let’s Encrypt will issue you a new certificate and bind it to the IIS website, and the automatic certificate renewal task will appear in the Task Scheduler.
You can manually export this certificate and bind it to the required RDS services through the SSL binding. But you will have to perform these steps manually every 60 days when the Let’s Encrypt certificate is renewed.
We can use the PowerShell script to automatically bind the SSL certificate to the RDS Gateway after updating the Let’s Encrypt certificate.
There is a ready PowerShell script in the win-acme project – ImportRDGateway.ps1 (https://github.com/PKISharp/win-acme/tree/master/dist/Scripts), which allows you to install the selected SSL certificate for Remote Desktop Services. The main drawback of this script is that you have to manually specify the thumbprint of the new certificate:
ImportRDGateway.ps1 <certThumbprint>
To automatically get the certificate thumbprint from the specified IIS site, use the modified script ImportRDGateway_Cert_From_IIS.ps1 (based on the ImportRDGateway.ps1).
You can run this script manually:
powershell -File ImportRDGateway_Cert_From_IIS.ps1
If your RDS Gateway runs on the IIS “Default Web Site” with index 0, you can use the script without changes.
Import-Module WebAdministration
Get-ChildItem IIS:Sites|ft -AutoSize
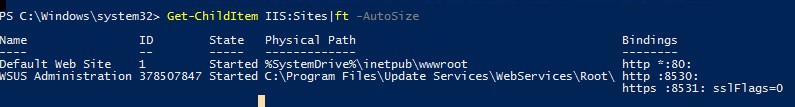
$NewCertThumbprint = (Get-ChildItem IIS:SSLBindings)[0].Thumbprint
Now open the win-acme-renew scheduler task, and on the Actions tab add a new task that runs the ImportRDGateway_Cert_From_IIS.ps1 script after updating the SSL certificate.
In order not to change the PowerShell execution policy, you can run the script with the command:
PowerShell.exe -ExecutionPolicy Bypass -File c:\inetpub\letsencrypt\ImportRDGateway_Cert_From_IIS.ps1
Now the script for binding the SSL certificate to the RDS will be executed immediately after the Let’s Encrypt certificate is renewed. In this case, the RD Gateway service is automatically restarted with the command:
Restart-Service TSGateway
[aler] When the TSGateway service restarts, all current user sessions are disconnected, so it is recommended to change the frequency of launching the certificate renewal task once every 60 days.[/alert]

10 comments
Hello,
Where would web.config be located? I know I can search for it, I just think it should be mentioned (it’s default location anyway) Thanks great little tutorial.
Default is in the root of the web directory.
Anywhere else is done by design.
I am hoping you can help me out. Please email me.
Scenario:
The issue we are facing is that clients would setup domains in an A record or CNAME like app.customerdomain.com pointed to our domain. That’s on our server like custom.elevatie.com which is binded.
We generate a certificate but where do we bind it because the certificate generated is for client domain which isn’t binded on our system because they have their CNAME/A Record pointed to our custom.elevatie.com to handle all the requests.
But if we were to physically bind the domain on the server and apply the certificate then yes we are able to obtain SSL. But this isn’t the case.
Is there any way to renew the SSL automatic, 30 days before and not 60 days?
Thanks for the guide,
Do you know if the URL Rewrite will break the ACME automated renewal?
I have not encountered such cases. Check your IIS and ACME log files.
Great post
most of free SSLs are 3 months
At Windows Server 2016 Essentials
$NewCertThumbprint = (Get-ChildItem IIS:SSLBindings\0.0.0.0!443)[0].Thumbprintand
$RdsSslCertThumbprint = (Get-Item -Path RDS:\GatewayServer\SSLCertificate\Thumbprint).CurrentValueif ($RdsSslCertThumbprint -ne $CertInStore.Thumbprint)
{
Set-Item -Path RDS:\GatewayServer\SSLCertificate\Thumbprint -Value $CertInStore.Thumbprint -ErrorAction Stop
Restart-Service TSGateway -Force -ErrorAction Stop
"Cert thumbprint set to RD Gateway listener and service restarted"
}
I have been getting a error now with the renewals.
Cert thumbprint was not set successfully
Error: Access to the object at RDS:\GatewayServer\SSLCertificate\Thumbprint is denied for the cmdlet Set-Item.The certificate is not valid or you do not have sufficient permissions to perform this operation.
Any ideas what can be causing it?
[…] un certificat émis par une autorité de confiance. On peut obtenir un certificat gratuit avec Let’s Encrypt ou bien le faire soi-même en PowerShell. C’est la voie que je vais […]