In this article, we will look at two ways to organize conditional name resolution in a DNS server on Windows Server 2016/2019/2022: DNS Conditional Forwarding and DNS Policies. These technologies allow you to configure conditional DNS name resolution based on the requested name, IP address, client location, time of day, etc.
DNS Conditional Forwarding allows to forward DNS requests about a particular domain to specific DNS servers. Usually, Conditional Forwarders are used when you want to configure fast name resolution between multiple private internal domains, or if you do not want DNS requests from your server to be sent through the Internet. In this case, you can create a rule on your DNS server to forward DNS requests for a particular domain zone (only!!!) to a specified DNS server.
How to Configure DNS Conditional Forwarder on Windows Server?
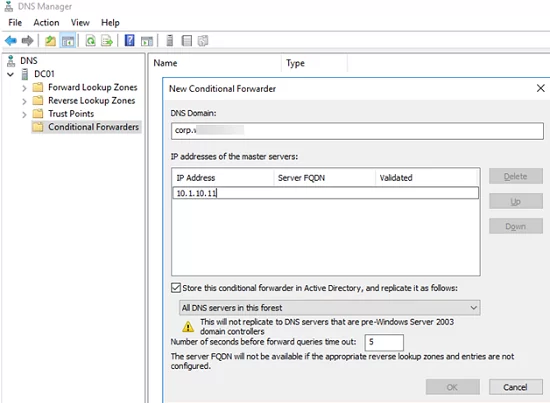
Let’s try to configure DNS conditional forwarding for a specific domain zone on Windows Server 2019. For example, all DNS requests to corp.woshub.com zone should be forwarded to the DNS server 10.1.10.11.
- Open the DNS management console (
dnsmgmt.msc); - Expand your DNS server, right-click Conditional Forwarders, and select New Conditional Forwarder;
- Enter the FQDN of the domain for which you want to enable conditional forwarding in the DNS domain field;
- Specify the IP address of the DNS server to which all requests for the specified namespace should be forwarded in the IP addresses of the master servers field;
- If you want to store a conditional forwarding rule on more than just this one DNS server, you can integrate it with AD. Check the option Store this conditional forwarder in Active Directory;
- Configure the conditional forwarding replication option (All DNS servers in this forest, All DNS servers in this domain, or All domain controllers in this domain).
Configure DNS Conditional Forwarding with PowerShell
You can create a Conditional Forwarder rule for a DNS zone using PowerShell. Use the Add-DnsServerConditionalForwarderZone cmdlet:
Add-DnsServerConditionalForwarderZone -Name dmz.woshub.com -MasterServers 192.168.1.11,192.168.101.11 -ReplicationScope Forest
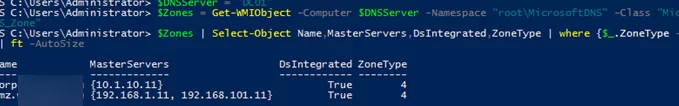
Run the following PowerShell script to list DNS conditional forwarders on a specific server:
$DNSServer = "DC01"
$Zones = Get-WMIObject -Computer $DNSServer -Namespace "root\MicrosoftDNS" -Class "MicrosoftDNS_Zone"
$Zones | Select-Object Name,MasterServers,DsIntegrated,ZoneType | where {$_.ZoneType -eq "4"} | ft -AutoSize
Filter DNS Queries with the Windows Server DNS Policies
Windows Server 2016 adds a DNS policy feature to the DNS server. DNS Policies allow you to configure the DNS server to return different responses to DNS queries depending on where you’re located (depending on the IP address or subnet from which the request was sent), the interface of the DNS server, the time of day, the type of record requested (A, CNAME, PTR, MX), etc. DNS policies in Windows Server allow you to implement load balancing, DNS traffic filtering, DNS record return based on geographic location (client IP address), and other complex scenarios.
You can create a policy at the level of a DNS server or a specific domain zone. The configuration of DNS policies in Windows Server can only be done from the PowerShell command line.
Let’s try to create a simple policy that returns a different response to a DNS query depending on the location of a client. Suppose you want clients in each branch to use their local proxy server on a site.
You have created a GPO to configure proxy settings in the domain (proxy.woshub.com will be specified on all clients). However, in order to use their local proxy server, clients from different offices need to resolve this FQDN differently.
I have created 3 subnets for company branches:
Add-DnsServerClientSubnet -Name "BER_DNS_Subnet" -IPv4Subnet "192.168.1.0/24"
Add-DnsServerClientSubnet -Name "HH_DNS_Subnet" -IPv4Subnet "192.168.11.0/24"
Add-DnsServerClientSubnet -Name "MCH_DNS_Subnet" -IPv4Subnet "192.168.21.0/24"
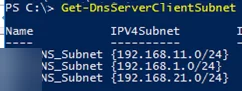
-ComputerName dc01 option.List all available IP subnets on the DNS server:
Get-DnsServerClientSubnet
Now you need to create a separate DNS zone for each office:
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "BERZoneScope"
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "HHZoneScope"
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "MCHZoneScope"
The following commands will add 3 DNS records with the same name pointing to different IP addresses in different DNS zones:
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.1.10" -ZoneScope "BERZoneScope"
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.11.10" -ZoneScope "HHZoneScope"
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.21.10" -ZoneScope "MCHZoneScope"
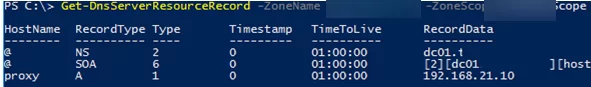
Get-DnsServerResourceRecord -ZoneName "woshub.com" -ZoneScope BERZoneScope
Then create DNS policies that bind IP subnets, DNS zones, and A records.
Add-DnsServerQueryResolutionPolicy -Name BERResolutionPolicy -Action ALLOW -ClientSubnet "eq,BER_DNS_Subnet" -ZoneScope "BERZoneScope,1" -ZoneName woshub.com –PassThru
Add-DnsServerQueryResolutionPolicy -Name HHResolutionPolicy -Action ALLOW -ClientSubnet "eq,HH_DNS_Subnet" -ZoneScope "HHZoneScope,1" -ZoneName woshub.com -PassThru
Add-DnsServerQueryResolutionPolicy -Name MCHResolutionPolicy -Action ALLOW -ClientSubnet "eq,MCH_DNS_Subnet" -ZoneScope "MCHZoneScope,1" -ZoneName woshub.com –PassThru
-Action ALLOW-Action DENY-Action IGNORE
You can use the following options in your DNS filters:
-InternetProtocol "EQ,IPv4,NE,IPv6"
-TransportProtocol "EQ,UDP,TCP"
-ServerInterfaceIP "EQ,192.168.1.21"
-QType "EQ,A,AAAA,NE,PTR"
-TimeOfDay "EQ,9:00-18:00"
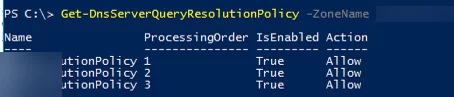
You can display a list of DNS policies for a DNS zone on the server:
Get-DnsServerQueryResolutionPolicy -ZoneName woshub.com
Now check that the DNS server returns different proxy IP addresses for the same request sent from devices in different offices:
nslookup proxy.woshub.com
You can prevent your DNS server from returning DNS addresses for a namespace (domain):
Add-DnsServerQueryResolutionPolicy -Name 'BlockDNSQuery' -Action IGNORE -FQDN "EQ,*.spamorg.org"
2 comments
Hi!
Thank for article, it’s so helpful.
DNS Policy looks cool. But I notice one “undocumented feature”😃: if there are exist any DNS-records in Default Zone scope of woshub.com DNS-zone, client under resolution policy (for example clients from BER_DNS_Subnet which under policy BERResolutionPolicy) can’t resolve record from Default Zone scope of woshub.com DNS-zone. Did you face with it?
Adding this option (-Fqdn “eq,proxy.woshub.com”) fixed my problem.
Add-DnsServerQueryResolutionPolicy -Name BERResolutionPolicy -Action ALLOW -ClientSubnet “eq,BER_DNS_Subnet” -ZoneScope “BERZoneScope,1” -ZoneName woshub.com –PassThru -Fqdn “eq,proxy.woshub.com”
Add-DnsServerQueryResolutionPolicy -Name HHResolutionPolicy -Action ALLOW -ClientSubnet “eq,HH_DNS_Subnet” -ZoneScope “HHZoneScope,1” -ZoneName woshub.com -PassThru -Fqdn “eq,proxy.woshub.com”
Add-DnsServerQueryResolutionPolicy -Name MCHResolutionPolicy -Action ALLOW -ClientSubnet “eq,MCH_DNS_Subnet” -ZoneScope “MCHZoneScope,1” -ZoneName woshub.com –PassThru -Fqdn “eq,proxy.woshub.com”